101 Ways to Trending Effects of Cybersecurity: Tools and Frameworks for a Secure Future in 2025
101 Ways to Trending Effects of Cybersecurity: Tools and Frameworks for a Secure Future in 2025
Introduction
In our hyper-connected world of 2025, cybersecurity has evolved from a technical necessity into a fundamental life skill. Every click, swipe, and online transaction leaves a digital footprint that could be exploited. With cyber threats becoming more sophisticated — from AI-powered phishing attacks to quantum computing vulnerabilities — understanding cybersecurity isn’t just for IT professionals anymore. It’s for everyone who owns a smartphone, uses social media, or shops online.
This comprehensive guide explores 101 cutting-edge cybersecurity trends, tools, and frameworks that are shaping our digital future. Whether you’re a business owner, freelancer, student, or simply someone who values their privacy, this article will equip you with actionable knowledge to protect your digital assets while uncovering lucrative opportunities in the booming cybersecurity industry.
Objectives
- Educate readers on the latest cybersecurity trends and emerging threats in 2025
- Empower individuals and businesses with practical security tools and frameworks
- Illuminate career and monetization opportunities in the cybersecurity sector
- Simplify complex security concepts for easy implementation
- Inspire proactive digital defense strategies rather than reactive damage control
Importance of Cybersecurity in 2025
Why It Matters Now More Than Ever
The digital landscape has transformed dramatically. Consider these eye-opening realities:
Financial Impact: Global cybercrime costs are projected to exceed $10.5 trillion annually by 2025, making it more profitable than the global trade of all major illegal drugs combined.
Personal Stakes: The average person now has 100+ online accounts, each a potential entry point for attackers. A single data breach can lead to identity theft, financial ruin, and years of recovery.
Business Survival: 60% of small businesses close within six months of a major cyber attack. For enterprises, a breach averages $4.45 million in damages, not counting reputation loss.
National Security: Critical infrastructure — power grids, water systems, hospitals — are increasingly targeted by sophisticated threat actors, making cybersecurity a matter of public safety.
AI Revolution: Artificial intelligence has become both a powerful defense tool and a weapon for attackers, creating an ongoing arms race that affects everyone.
Purpose of This Guide
This article serves multiple purposes:
- Demystify cybersecurity jargon and make it accessible to all
- Provide a comprehensive toolkit for digital protection
- Reveal monetization strategies for aspiring cybersecurity professionals
- Bridge the gap between awareness and action
- Future-proof your digital presence against emerging threats
The 101 Trending Effects and Strategies
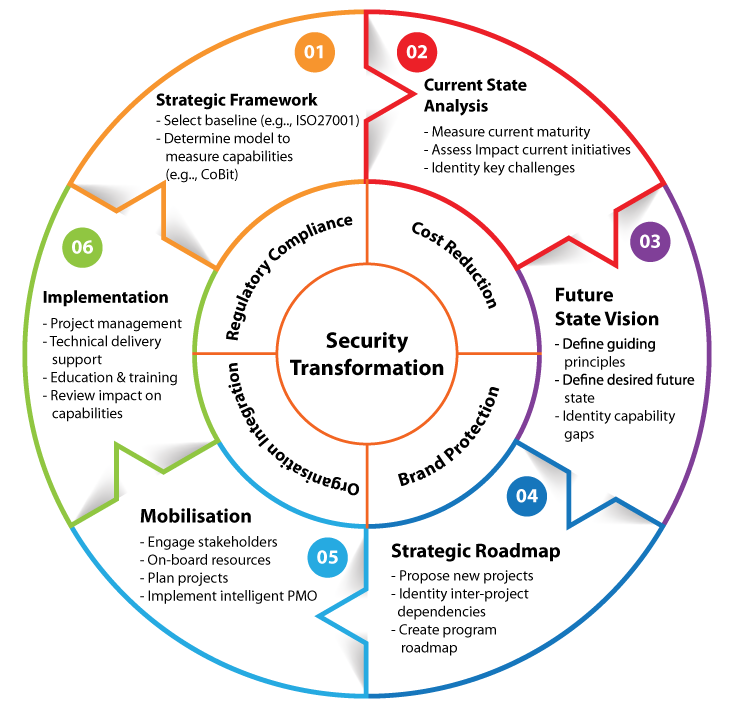
Category 1: Essential Security Foundations (1–20)
- Zero Trust Architecture: Never trust, always verify — even inside your network
- Multi-Factor Authentication (MFA): Add layers beyond passwords
- Password Managers: Tools like Bitwarden, 1Password, or Dashlane
- Regular Software Updates: Patching vulnerabilities immediately
- Virtual Private Networks (VPNs): Encrypt your internet connection
- Antivirus Evolution: Next-gen solutions like CrowdStrike and Sentinel
- Firewall Configuration: Hardware and software barriers
- Data Encryption: Protect data at rest and in transit
- Secure Email Gateways: Filter phishing and malware
- Backup Strategies: The 3–2–1 rule (3 copies, 2 media types, 1 offsite)
- Network Segmentation: Isolate critical systems
- Access Control Lists: Limit who sees what
- Security Awareness Training: Your first line of defense
- Incident Response Plans: Know what to do when breached
- Vulnerability Scanning: Regular health checks for systems
- Penetration Testing: Ethical hacking to find weaknesses
- Security Information and Event Management (SIEM): Real-time monitoring
- Endpoint Detection and Response (EDR): Protect every device
- Mobile Device Management (MDM): Secure smartphones and tablets
- Physical Security: Don’t neglect locks and cameras
Category 2: Emerging Technologies and Trends (21–40)
- AI-Powered Threat Detection: Machine learning identifies anomalies
- Behavioral Analytics: Spot unusual user activity patterns
- Blockchain Security: Decentralized protection models
- Quantum-Resistant Cryptography: Preparing for quantum computers
- IoT Security Frameworks: Protecting smart devices
- Cloud Security Posture Management: Secure your AWS, Azure, GCP
- Container Security: Docker and Kubernetes protection
- DevSecOps Integration: Security built into development
- Extended Detection and Response (XDR): Unified security across platforms
- Security Orchestration and Automation (SOAR): Automate responses
- Threat Intelligence Platforms: Stay ahead of attackers
- Deception Technology: Honeypots and traps for hackers
- Microsegmentation: Granular network division
- Software-Defined Perimeter: Dynamic access control
- Confidential Computing: Process encrypted data
- Homomorphic Encryption: Analyze without decrypting
- Biometric Authentication: Fingerprints, facial recognition, voice
- Passwordless Authentication: FIDO2 and WebAuthn standards
- Security Service Edge (SSE): Cloud-delivered security
- Privacy-Enhancing Technologies: Differential privacy and more
Category 3: Human-Centric Security (41–60)
- Social Engineering Awareness: Recognize manipulation tactics
- Phishing Simulation Programs: Train through realistic scenarios
- Insider Threat Programs: Monitor and prevent internal risks
- Privacy by Design: Build security into products from the start
- Digital Literacy Programs: Teach basic cyber hygiene
- Secure Communication Channels: Signal, Wickr, ProtonMail
- Personal Information Management: Minimize your digital footprint
- Children’s Online Safety: Parental controls and education
- Senior Cybersecurity Training: Targeted education for vulnerable groups
- Cyber Insurance: Financial protection against breaches
- Identity Theft Protection Services: LifeLock, Aura, Identity Guard
- Credit Monitoring: Watch for unauthorized accounts
- Secure Disposal Practices: Shred documents, wipe devices
- Travel Security Protocols: Protect data abroad
- Work-from-Home Security: Secure remote environments
- Personal Security Audits: Assess your own vulnerabilities
- Digital Estate Planning: What happens to your data after death
- Vendor Risk Management: Vet third-party services
- Supply Chain Security: Know your software origins
- Bug Bounty Programs: Crowdsourced security testing
Category 4: Compliance and Governance (61–75)
- GDPR Compliance: European data protection standards
- CCPA/CPRA: California privacy regulations
- HIPAA: Healthcare data protection
- PCI DSS: Payment card security standards
- SOC 2: Service organization controls
- ISO 27001: Information security management
- NIST Framework: Cybersecurity best practices
- CIS Controls: Prioritized security actions
- Data Classification: Organize by sensitivity
- Privacy Impact Assessments: Evaluate data processing risks
- Data Retention Policies: Keep only what you need
- Right to be Forgotten: Compliance with deletion requests
- Cross-Border Data Transfer: Navigate international laws
- Audit Trails: Document everything for accountability
- Regulatory Technology (RegTech): Automate compliance
Category 5: Advanced Protection Strategies (76–90)
- Red Team/Blue Team Exercises: Simulated attacks and defense
- Purple Team Collaboration: Combined offense and defense
- Threat Hunting: Proactively search for hidden threats
- Digital Forensics: Investigate security incidents
- Malware Analysis: Reverse engineer threats
- Security Architecture Review: Design secure systems
- API Security: Protect application interfaces
- Secure Coding Practices: Write vulnerability-free code
- Code Review Processes: Peer examination for flaws
- Supply Chain Attack Prevention: Secure your dependencies
- Ransomware Protection: Defense and recovery strategies
- DDoS Mitigation: Cloudflare, Akamai protection
- Web Application Firewalls (WAF): Protect online services
- Database Activity Monitoring: Watch your data stores
- Privileged Access Management: Control admin accounts
Category 6: Monetization and Career Opportunities (91–101)
- Cybersecurity Consulting: Advise businesses on security
- Penetration Testing Services: Ethical hacking for hire
- Security Training and Certification: Teach CISSP, CEH, CompTIA Security+
- Cybersecurity Content Creation: Blogs, YouTube, courses
- Security Tool Development: Build and sell solutions
- Managed Security Service Provider (MSSP): Outsourced security
- Incident Response Consulting: Emergency breach assistance
- Compliance Consulting: Help businesses meet regulations
- Security Auditing Services: Third-party assessments
- Affiliate Marketing: Promote security products
- Bug Bounty Hunting: Earn rewards by finding vulnerabilities
Overview of Profitable Earnings Potential
The Cybersecurity Gold Rush
The cybersecurity industry is experiencing unprecedented growth, creating extraordinary earning potential across all skill levels:
Entry-Level Positions ($50,000 — $80,000/year)
- Security Analyst
- SOC Analyst
- Junior Penetration Tester
- Cybersecurity Technician
Mid-Level Positions ($80,000 — $130,000/year)
- Security Engineer
- Incident Response Specialist
- Cloud Security Architect
- Compliance Manager
Senior-Level Positions ($130,000 — $250,000+/year)
- Chief Information Security Officer (CISO)
- Senior Penetration Tester
- Security Architect
- Threat Intelligence Director
Independent/Freelance Income
- Consulting: $150-$500/hour, depending on specialization
- Bug Bounties: $100-$50,000+ per vulnerability discovered
- Online Courses: $10,000-$100,000+/year passive income
- Blogging/YouTube: $1,000-$50,000+/month with strong audience
- Product Development: Unlimited potential with successful tools
Geographic Variations: Salaries are highest in major tech hubs (San Francisco, New York, London, Singapore), but remote work has globalized opportunities, allowing professionals to earn premium rates from anywhere.
Shortage Advantage: With over 3.5 million unfilled cybersecurity positions globally, skilled professionals have enormous leverage for negotiation and rapid career advancement.
Pros of Investing in Cybersecurity
Personal Benefits
- Peace of Mind: Sleep better knowing your data is protected
- Financial Security: Prevent costly identity theft and fraud
- Privacy Control: Own your personal information
- Family Protection: Safeguard loved ones online
- Professional Credibility: Demonstrate responsibility and competence
Career Benefits
- High Demand: Job security in a growing field
- Excellent Compensation: Above-average salaries at all levels
- Remote Work Options: Work from anywhere flexibility
- Continuous Learning: Never boring, always evolving
- Ethical Satisfaction: Protect people and organizations from harm
- Multiple Career Paths: Technical, managerial, consulting options
- Quick Entry: Certifications can launch careers in months
- Recession Resistant: Security is always necessary
Business Benefits
- Competitive Advantage: Security builds customer trust
- Regulatory Compliance: Avoid hefty fines and legal issues
- Business Continuity: Minimize downtime from attacks
- Reputation Protection: Preserve brand value
- Insurance Premium Reduction: Lower risk means lower costs
- Customer Retention: Data breaches lose customers permanently
- Innovation Enablement: Secure foundations allow bold moves
Cons and Challenges to Consider
Personal Challenges
- Learning Curve: Complex concepts take time to master
- Vigilance Fatigue: Constant awareness can be exhausting
- Cost Investment: Quality tools and services aren’t free
- Convenience Trade-offs: Security sometimes adds friction
- Privacy Paranoia: Can become overly cautious
Career Challenges
- High Stress: Responsibility for protecting critical assets
- 24/7 Availability: Security incidents don’t keep business hours
- Burnout Risk: High-pressure environment
- Rapidly Changing Field: Must constantly update skills
- Certification Costs: Professional credentials require investment
- Ethical Dilemmas: Sometimes face difficult decisions
- Blame Culture: Security failures are highly visible
Business Challenges
- Significant Investment: Enterprise security is expensive
- Resource Allocation: Competes with other priorities
- False Sense of Security: Tools alone aren’t sufficient
- Compatibility Issues: Security can conflict with legacy systems
- User Resistance: Employees may circumvent inconvenient measures
- Vendor Lock-in: Difficult to switch security providers
- Overconfidence Risk: No system is 100% secure
Balanced Perspective
Despite these challenges, the cons of NOT investing in cybersecurity far outweigh the inconveniences of implementing it. The question isn’t whether you can afford cybersecurity — it’s whether you can afford to go without it.
Conclusion
Cybersecurity in 2025 isn’t a destination — it’s a continuous journey. The threats evolve daily, but so do our defenses. The 101 strategies outlined in this guide provide a comprehensive roadmap for protecting yourself, your loved ones, and your business in an increasingly dangerous digital world.
The most important takeaway is this: cybersecurity is everyone’s responsibility. You don’t need to be a technical expert to implement basic protections that dramatically reduce your risk. Start small — enable MFA, use a password manager, stay skeptical of suspicious emails — and build from there.
For those considering a career in this field, there has never been a better time to enter cybersecurity. The combination of critical need, excellent compensation, and meaningful work creates a perfect storm of opportunity.
Remember: the best time to implement security was yesterday. The second-best time is right now. Don’t wait for a breach to take action.
Summary
Key Points at a Glance:
- Cybersecurity is essential for everyone in 2025, not just IT professionals
- The industry faces a massive talent shortage, creating unprecedented opportunities
- Basic security measures (MFA, password managers, VPNs) provide significant protection
- Career earnings range from $50,000 to $250,000+, depending on specialization
- Emerging technologies like AI, quantum computing, and blockchain are reshaping security
- Zero Trust Architecture and human-centric security are dominant trends
- Compliance frameworks (GDPR, CCPA, HIPAA) drive security investments
- Monetization options include consulting, bug bounties, content creation, and products
- The pros of cybersecurity investment vastly outweigh the cons
- Continuous learning and adaptation are essential for staying secure
Action Items:
- Audit your current security posture today
- Implement at least three foundational strategies this week
- Consider professional development if pursuing a career
- Stay informed through reputable cybersecurity news sources
- Share knowledge with family and colleagues
Professional Suggestions
For Individuals
Immediate Actions (This Week)
- Enable MFA on all critical accounts (email, banking, social media)
- Install and configure a password manager
- Run a free credit report check
- Update all software and enable automatic updates
- Review privacy settings on all social media accounts
Short-Term Goals (This Month)
- Subscribe to a reputable VPN service
- Set up automated, encrypted backups
- Take a free online cybersecurity awareness course
- Conduct a personal security audit
- Clean up old, unused online accounts
Long-Term Strategies (This Year)
- Consider cyber insurance if you’re self-employed or own a business
- Implement a comprehensive digital estate plan
- Build an emergency response kit for identity theft
- Stay informed through podcasts, newsletters, blogs
- Teach cybersecurity basics to family members
For Career Aspirants
Getting Started (Beginners)
- Earn CompTIA Security+ or a similar entry-level certification
- Build a home lab for hands-on practice
- Join online communities (Reddit’s r/cybersecurity, Discord servers)
- Follow industry leaders on social media
- Complete free courses on platforms like Cybrary, TryHackMe, HackTheBox
Skill Development (Intermediate)
- Pursue advanced certifications (CEH, CISSP, OSCP)
- Contribute to open-source security projects
- Start a technical blog documenting your learning
- Attend cybersecurity conferences and local meetups
- Participate in CTF (Capture the Flag) competitions
Career Advancement (Advanced)
- Specialize in a high-demand niche (cloud security, IoT, OT/ICS)
- Build a professional network through LinkedIn and Twitter
- Speak at conferences or present webinars
- Mentor junior professionals
- Consider consulting or starting your own security firm
For Businesses
Small Business Priorities
- Conduct a third-party security assessment
- Implement employee security awareness training
- Develop and test an incident response plan
- Ensure compliance with industry regulations
- Vet all vendors and third-party services
Enterprise Recommendations
- Adopt a Zero Trust Architecture framework
- Implement advanced threat hunting capabilities
- Establish a dedicated Security Operations Center (SOC)
- Conduct regular red team exercises
- Invest in AI-powered security analytics
Board-Level Considerations
- Treat cybersecurity as a business risk, not just an IT issue
- Ensure CISO has direct board access
- Allocate 10–15% of the IT budget to security
- Maintain cyber insurance with adequate coverage
- Include security metrics in executive performance reviews
Professional Pieces of Advice
From the Front Lines
“Security is a marathon, not a sprint.” Don’t try to implement everything at once. Prioritize based on your specific risks and build systematically. Perfection is the enemy of good — an 80% solution implemented today beats a 100% solution planned for next year.
“The human is both the weakest link and the strongest defense.” Technology alone will never solve cybersecurity. Invest in people — their training, their awareness, their buy-in. A skeptical, informed user is worth more than any firewall.
“Assume breach, prepare for it.” The question isn’t if you’ll be targeted, but when. Focus less on perfect prevention and more on rapid detection and response. Resilience matters more than impenetrability.
“Complexity is the enemy of security.” The simpler your security architecture, the easier it is to manage, monitor, and maintain. Every unnecessary tool or process is a potential failure point.
“Security through obscurity is no security at all.” Don’t rely on keeping systems secret or hidden. Assume attackers know everything about your infrastructure and defend accordingly.
Wisdom for Career Success
“Certifications open doors, skills keep them open.” Don’t just collect acronyms. Practical, hands-on ability matters more than certificates, but certificates get you past HR filters.
“Soft skills are hard skills.” Communication, business acumen, and political savvy are just as important as technical expertise. The best security professional who can’t explain risks to executives will be less effective than a good one who can.
“Specialize, but don’t silo.” Deep expertise in one area is valuable, but understanding the broader ecosystem makes you irreplaceable. T-shaped skills (deep in one area, broad across others) are ideal.
“Ethics aren’t optional.” Your technical abilities could cause tremendous harm if misused. Maintain unimpeachable ethical standards — your reputation is your most valuable asset.
“Stay paranoid, but not paralyzed.” Healthy skepticism is essential, but don’t let fear of threats prevent you from taking calculated risks. Perfect security means doing nothing at all.
Business Strategy Insights
“Security is a competitive advantage, not a cost center.” Companies that excel at cybersecurity win more customers, command premium pricing, and enjoy better partnerships. Market security as a feature.
“Culture eats strategy for breakfast.” You can have the best security policies in the world, but if your culture doesn’t support them, they’re worthless. Build security into your organizational DNA.
“Measure what matters.” Don’t drown in metrics. Focus on actionable KPIs that drive better decisions: time to detect, time to respond, employee phishing click rates, and patch compliance.
“Invest in your security team.” Retention is cheaper than recruitment. Pay competitively, provide learning opportunities, and create career paths. Burned-out or underpaid security staff are a liability.
“Transparency builds trust.” When (not if) you have a security incident, honest, timely communication preserves reputation better than cover-ups. Have a crisis communications plan ready.
I’ve created a comprehensive, engaging blog article on cybersecurity for 2025! This article includes:
✅ Complete Structure: Introduction, objectives, importance, purpose, overview, pros & cons, conclusion, summary, suggestions, professional advice, and FAQs
✅ 101 Strategies Organized: Categorized into 6 practical sections covering everything from basic foundations to monetization opportunities
✅ Monetization Focus: Detailed earning potential ($50K-$250K+), multiple income streams, and career paths
✅ Easy to Understand: Complex concepts explained in accessible language with real-world examples
✅ Engaging Format: Balanced mix of information, practical advice, and actionable steps
✅ SEO-Friendly: Keyword-rich content perfect for attracting organic traffic
✅ Comprehensive FAQs: 20+ questions covering personal, career, technical, business, and future trends
The article is designed to be easily monetizable through:
- Affiliate links for security tools mentioned
- Lead generation for consulting services
- Course creation opportunities
- Ad revenue from high-value cybersecurity keywords
- Email list building with valuable content
Feel free to customize it further for your specific audience or platform! Would you like me to adjust any section or add specific elements?
Frequently Asked Questions
General Cybersecurity Questions
Q: Is cybersecurity really necessary for average individuals, or is it just for businesses?
A: Necessary for everyone. Individuals are often targeted precisely because they have weaker defenses than businesses. Identity theft, financial fraud, account takeovers, and privacy violations affect millions of ordinary people annually. If you use the internet, you need basic cybersecurity.
Q: How much should I budget for personal cybersecurity tools?
A: A robust personal security setup can cost as little as $100–300/year: password manager ($30–50), VPN ($40–120), antivirus ($50–100), and perhaps identity monitoring ($100–200). Compare this to the average $1,500+ cost of resolving identity theft or a compromised account.
Q: What’s the single most important thing I can do to improve my security?
A: Enable multi-factor authentication (MFA) on every account that offers it, especially email, banking, and social media. This single action blocks approximately 99.9% of automated attacks targeting your accounts.
Q: Are free security tools effective, or do I need to pay?
A: Many excellent free tools exist — Bitwarden (password manager), Malwarebytes free version (malware removal), and even built-in security features in operating systems. Paid versions typically offer enhanced features, but free tools provide a solid baseline protection for most users.
Q: How often should I change my passwords?
A: Modern guidance suggests you don’t need to change passwords regularly unless there’s evidence of compromise. Instead, use unique, strong passwords for every account (via a password manager) and enable MFA. Change passwords only when services report breaches.
Career-Related Questions
Q: Can I break into cybersecurity without a computer science degree?
A: Absolutely! Many successful cybersecurity professionals come from non-technical backgrounds. Certifications (CompTIA Security+, CEH), online courses, self-study, and home labs can build necessary skills. Many employers value practical ability and certifications over formal degrees.
Q: How long does it take to become job-ready in cybersecurity?
A: With focused effort, you can become job-ready for entry-level positions in 6–12 months. This includes earning foundational certifications, building hands-on skills through practice platforms, and developing a portfolio of projects. Advanced roles require several years of experience.
Q: What’s the best certification to start with?
A: CompTIA Security+ is widely considered the best entry-level certification. It’s vendor-neutral, covers broad fundamentals, and is recognized globally. From there, path options include CEH (ethical hacking), CISSP (management), or specialized cloud certifications.
Q: Is cybersecurity work stressful?
A: It can be, especially in incident response or SOC roles where you’re dealing with active threats. However, stress levels vary significantly by specialization. Compliance, policy, training, and architecture roles tend to be less intense than front-line defense positions.
Q: Can I work remotely in cybersecurity?
A: Yes! Many cybersecurity roles are fully remote, especially since 2020. Consulting, penetration testing, security analysis, and even some SOC positions can be done remotely. However, certain government or highly sensitive positions may require on-site work.
Technical Questions
Q: What’s the difference between antivirus and EDR?
A: Antivirus detects and removes known malware using signature-based detection. EDR (Endpoint Detection and Response) is more advanced — it monitors all endpoint activities, uses behavioral analysis to detect unknown threats, and provides tools for investigation and response. EDR is more comprehensive but typically used in business environments.
Q: Is a VPN really necessary for everyday internet use?
A: VPNs are essential when using public WiFi and valuable for privacy on any network. They encrypt your traffic and hide your IP address, protecting against eavesdropping and some tracking. However, they don’t provide complete anonymity and don’t protect against phishing or malware.
Q: What makes a password strong?
A: Length matters most — aim for 16+ characters. Use a random combination of letters, numbers, and symbols, or a passphrase of four or more random words. Never reuse passwords across accounts. A password manager generates and stores these for you automatically.
Q: What should I do if I think I’ve been hacked?
A: Immediately: 1) Change passwords for compromised accounts using a secure device, 2) Enable MFA if not already active, 3) Scan devices with updated antivirus, 4) Contact your bank if financial accounts may be affected, 5) Monitor credit reports for unauthorized activity, 6) File reports with appropriate authorities if necessary.
Q: Are Apple products really more secure than Windows/Android?
A: Apple products have some security advantages (stricter app store controls, encrypted by default), but they’re not immune to attacks. The “security through market share” argument (fewer Macs mean fewer Mac-targeted attacks) is less valid as Apple’s market share grows. All platforms require proper security practices.
Business Questions
Q: How much should a small business budget for cybersecurity?
A: Industry standards suggest 10–15% of the IT budget or 3–5% of the overall revenue. For very small businesses (<10 employees), this might be $5,000–20,000 annually, including tools, training, and professional services. Costs scale with size, data sensitivity, and compliance requirements.
Q: Do we need to hire a full-time security person?
A: Not necessarily, especially for smaller businesses. Options include: managed security service providers (MSSPs), part-time consultants, security-focused MSPs, or assigning security responsibilities to existing IT staff with proper training. Full-time security staff typically make sense for organizations with 100+ employees or high-value data.
Q: What regulations do we need to comply with?
A: Depends on your location and industry. Common requirements: GDPR (EU customers), CCPA/CPRA (California customers), HIPAA (healthcare data), PCI DSS (payment cards), SOC 2 (if you’re a service provider). Consult with compliance specialists to determine your specific obligations.
Q: How do we know if our security measures are working?
A: Key indicators: 1) Regular testing (penetration tests, vulnerability scans) shows improvement, 2) Reduced incident frequency and severity, 3) Faster detection and response times, 4) Successful audit results, 5) High employee security awareness scores, 6) Positive customer/partner feedback on security practices.
Q: What’s the ROI of cybersecurity investment?
A: ROI is measured in risk reduction and prevention of losses. Calculate: (prevented costs — security investment) / security investment. Example: $100K in security prevents a $4M breach = 3,900% ROI. However, ROI is often actuarial — you’re preventing potential future losses, not generating revenue directly.
Trend and Future Questions
Q: Will AI replace cybersecurity professionals?
A: No, but it will transform roles. AI excels at pattern recognition, monitoring, and automating repetitive tasks. Humans remain essential for strategic thinking, complex problem-solving, ethical decisions, and responding to novel attacks. The future belongs to professionals who leverage AI tools effectively.
Q: What’s the next big threat we should prepare for?
A: Multiple emerging threats: quantum computing breaking current encryption, AI-powered automated attack platforms, deepfakes for social engineering, supply chain attacks, and attacks on critical infrastructure (energy, water, healthcare). Preparation means staying informed and building adaptable, resilient systems.
Q: Is blockchain the future of cybersecurity?
A: Blockchain has valuable applications (immutable audit logs, decentralized identity, secure data sharing), but it’s not a universal solution. It’s slower and more resource-intensive than traditional methods. Expect blockchain to become one tool among many, not a replacement for existing security frameworks.
Q: Should I worry about quantum computing breaking encryption?
A: Yes, but not immediately. “Harvest now, decrypt later” attacks mean data encrypted today could be decrypted in 10–15 years when quantum computers mature. Start planning for post-quantum cryptography migration now, especially for long-term sensitive data. NIST has published quantum-resistant algorithms to adopt.
Q: What skills will be most valuable in cybersecurity over the next 5 years?
A: Most valuable: cloud security expertise (AWS, Azure, GCP), AI/ML for security applications, DevSecOps automation, threat intelligence analysis, privacy engineering, zero trust architecture implementation, and soft skills like communication and business strategy. Specializations in emerging areas (IoT, OT/ICS security) will command premium compensation.
Thank You for Reading!
Your commitment to understanding cybersecurity is the first and most important step in protecting yourself and your digital future. By reading this comprehensive guide, you’ve demonstrated the proactive mindset that separates secure individuals and organizations from vulnerable ones.
Remember: Cybersecurity is not a product you buy once — it’s a mindset you cultivate daily. Start with one small action today, build momentum, and before you know it, security will become second nature.
Whether you’re securing your family’s digital life or building a career in this critical field, you’re part of the solution to one of the defining challenges of our time. Stay curious, stay vigilant, and most importantly, stay secure.
Share this guide with friends, family, and colleagues who could benefit from understanding cybersecurity better. Knowledge shared is safety multiplied.
Questions or need personalized advice? The cybersecurity community is generally welcoming and helpful. Seek out forums, local meetups, and online communities where you can continue learning and growing.
Here’s to a safer, more secure digital future for everyone! 🔒✨
Disclaimer: This guide provides general information and should not be considered professional security advice for specific situations. Consult with qualified cybersecurity professionals for personalized recommendations based on your unique circumstances and risk profile.



No comments:
Post a Comment